Featured Post
New Features of EasyBilling Invoicing Software in 2024 You Must Know
EasyBilling continues to push boundaries with its latest features introduced in 2024. These enhancements are designed to streamline your invoicing processes, boost productivity, and provide an unparalleled user experience. Let’s delve into the exciting new capabilities that EasyBilling now offers: 1. Document Template with Auto Create The new Document Template with Auto Create feature is a game-changer for time-saving automation. … Read more
Cheque Printing

The Asterisk and Cheque Security
A surprisingly important symbol, the asterisk plays a significant role in check security. Its strategic placement can deter fraud and ensure efficient processing of financial transactions. This article examines the reasoning behind the use of asterisks on checks and outlines best practices for their application. The Asterisk’s Role in Cheque Security The primary reason for placing asterisks before and after … Read more
Invoicing
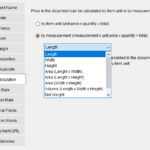
Beyond the Basics: Choosing Invoicing Software with Precision and Flexibility
Invoicing software is a cornerstone of any successful business, regardless of size or industry. While many offer basic features, powerful solutions offer features enhancing accuracy, efficiency, and adaptability. Two key areas are decimal point precision and flexible pricing options. The Importance of Decimal Point Precision: Minor pricing discrepancies accumulate, leading to significant financial inaccuracies. Advanced invoicing software handles decimal points … Read more
Thermal Printing

A Guide to Cleaning and Maintaining Your Thermal Receipt Printer
To ensure accurate receipt printing, thermal printers require proper maintenance, such as regular cleaning. But how do you clean a thermal printer? Here are some general steps and precautions. Before cleaning, always refer to your printer’s manual; incorrect procedures may affect printer operation. 1. Turn off and unplug Before cleaning, turn off the power and unplug the printer. 2. Gather … Read more
Email Marketing

Seven Effective Ways to Personalize Email Marketing Campaigns
Personalization is crucial in email marketing as it helps businesses tailor messages to individual recipients, increasing engagement, relevance, and ultimately conversion rates. Here are seven effective ways to personalize email marketing campaigns: 1. Personalized Email Subject Lines Use the recipient’s name or location in the email subject line to grab their attention and increase open rates. 2. Dynamic Content Customize … Read more
Office / Productivity

New Features of EasyBilling Invoicing Software in 2024 You Must Know
EasyBilling continues to push boundaries with its latest features introduced in 2024. These enhancements are designed to streamline your invoicing processes, boost productivity, and provide an unparalleled user experience. Let’s delve into the exciting new capabilities that EasyBilling now offers: 1. Document Template with Auto Create The new Document Template with Auto Create feature is a game-changer for time-saving automation. … Read more
SEO

Product Name Change? Don’t Forget Your SEO!
Renaming your product? Don’t forget SEO! Continuing to use your old product name in website URLs and image folders after a rebranding is detrimental to your search engine optimization (SEO). Here’s why, and how to fix it: The Problem: Conflicting Signals & Wasted Potential Changing a product name creates a significant SEO challenge. Search engines see the old and new … Read more
Traffic Generation
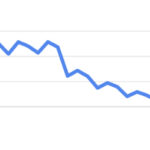
If search traffic drops, how to handle it?
Website traffic can come from different sources, such as search engines, social media sites, paid advertising, etc., among which search engines are the cheapest but also more difficult to control. Sometimes we may encounter situations where search traffic drops. What are the reasons behind this and how should we deal with it? Generally speaking, there are several main reasons for … Read more
Watermarking

Comparing different methods in protecting your photos in Internet
1. Provide Thumbnail instead of Original Pros: Give visitor a preview of your photo Cons: Thumbnail can be copied and spread widely in Internet. People can use the thumbnail freely. 2. Post an image with down grade quality Pros: Give visitor a preview of your photo Cons: It can be copied and spread widely in Internet. People can use the … Read more
Google Ads / PPC

Seven Tips for Using Google Ads Remarketing
Google Ads remarketing is a powerful online advertising tool that allows businesses to reconnect with users who have previously visited their website or used their apps. By tracking user behavior through cookies, remarketing enables businesses to display targeted ads to these past visitors as they browse other websites or platforms within the Google Display Network. This personalized approach aims to … Read more
Useful Website
Free photo websites, suitable for commercial use
When designing and managing website content, some images are always needed for decoration. Of course, we can create or take these photo images ourselves, but there are also many free image and photo libraries online, some of which explicitly state that they can be used for commercial purposes without the need to attribute the source. Below are several large photo … Read more
Useful Software
Monitor your website ranking in Google
Free Monitor for Google is a free search engine position software designed for SEO specialists and webmasters. Simply set your website address and add the target keywords into the software. It will query google search engines and show the search results. It will also the search result position of your web site. This simple tool allows you to set up … Read more
Security

Lock your computer with a USB Drive
Predator is a software which can lock your computer with a USB Drive. It generate a security code and place it on the USB Drive to identify it as the key. If the USB drive is unplugged, the program will lock your computer then. If someone attempts to access your PC while the USB stick is removed, a dialog is … Read more
